I always chase my DevOps team and seen lot many time we use to face below challenges
Overcoming a lack of visibility : We are running more applications on the cloud and also having more people to access those applications every day. Files change on a per-minute basis. Without a security strategy in place to keep track of this near-constant activity, it can be difficult to pick out what activity is malicious or suspicious.
Prioritizing a security strategy ahead of controls and tools : You must decide early on whether to implement a security strategy first or controls and tools. In most cases, having a strategy in place first will lead to smoother, more effective security from day one.
Improving confidence in a cloud provider security : Security on the cloud is becoming a discussion earlier in the cloud migration process. In that case you should always sit for discussion with AWS or your cloud security provider about compliance, accessing log data, dealing with incident response, and more.
Establishing who is accountable : In the event that a security incident does occur in your cloud environment, you want to know who is liable and what the appropriate actions are. AWS’ Shared Responsibility Model sheds light on this subject.
Understanding the lure behind cloud security attacks : When you operate in the cloud, you’re likely trusting a lot of sensitive data to your cloud provider. This makes it a great target for attacks. More often than not, security incidents occur because of credential threat, not sophisticated zero-day attack against cloud providers themselves.
Roles played by AWS in security AWS ensures the security of the AWS Global Infrastructure of 42 Availability Zones within 16 geographic Regions around the world, in addition to compute, storage, database, and networking capabilities. AWS is also responsible for the security configuration of their managed services including Amazon DynamoDB, Amazon Elastic MapReduce, and more. So basically they care about the components they are providing within there infra and you are utilizing it.
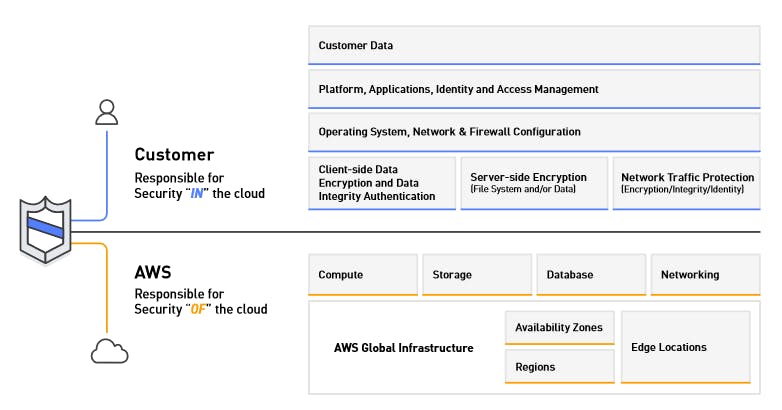
Roles we have to play You retain control and ownership over your data and what security you choose to implement to protect your own data, platform, applications, systems and networks, no differently than you would for applications in an on-site data center. This control over security implementations allows you to decide what security measures are necessary for your industry and organization, specifically
1. Leverage multi-factor authentication : Using a standard username and password combo as the sole gatekeeper between your data and hackers is no longer the safest bet. Securing access to your cloud applications with multi-factor authentication adds an additional safeguard against wrongful access. MFA requires users to take an extra step like receiving an access code on their phone or onetime passwords to complete the login process so that even if a hacker obtains login credentials, they aren’t able to log in.
One sample activity :
Step 1. Sign in to the AWS Management Console and open the IAM console at console.aws.amazon.com/iam
Step 2. In the navigation pane, choose Users.
Step 3. In the User Name list, choose the name of the intended MFA user.
Step 4. Choose the Security credentials tab. Next to Assigned MFA device, choose the edit icon ( ).
Step 5. In the Manage MFA Device wizard, choose A virtual MFA device, and then choose Next step.
Step 6. IAM generates and displays configuration information for the virtual MFA device, including a QR code graphic. The graphic is a representation of the 'secret configuration key' that is available for manual entry on devices that do not support QR codes. Open your virtual MFA app. (For a list of apps that you can use for hosting virtual MFA devices, see Virtual MFA Applications.) If the virtual MFA app supports multiple accounts (multiple virtual MFA devices), choose the option to create a new account (a new virtual MFA device).
Step 7. Determine whether the MFA app supports QR codes, and then do one of the following: Use the app to scan the QR code. For example, you might choose the camera icon or choose an option similar to Scan code, and then use the device's camera to scan the code. In the Manage MFA Device wizard, choose Show secret key for manual configuration, and then type the secret configuration key into your MFA app.
Step 8. When you are finished, the virtual MFA device starts generating one-time passwords. In the Manage MFA Device wizard, in the Authentication Code 1 box, type the one-time password that currently appears in the virtual MFA device. Wait up to 30 seconds for the device to generate a new one-time password. Then type the second one-time password into the Authentication Code 2 box. Choose Active Virtual MFA. Submit your request immediately after generating the codes. If you generate the codes and then wait too long to submit the request, the MFA device successfully associates with the user but the MFA device is out of sync. This happens because time-based one-time passwords (TOTP) expire after a short period of time. If this happens, you can resync the device.
2. Utilize identity and access management : Users expect to access your applications fast and with as few roadblocks as possible. As an organization, you must find the balance between streamlined access and secure data. Identity and access management (IAM) combines the three elements you need to achieve this: identification, authentication, and authorization.
3. Maintain strong visibility into your cloud environment : Blind spots are the enemy to any security posture. Having deep visibility into your cloud environment at all times is essential to maintaining operations, pinpointing issues, and adhering to compliance standards.
4. Implement end-to-end encryption : Cloud security should be more proactive than reactive. Encrypting data end-to-end is a proactive move that ensures that even if the worst happens—your data gets into the wrong hands—it’ll still be secure and unreadable.
5. Monitor file integrity : Establishing a known baseline and regularly monitoring file integrity helps alert you to unwanted or malicious changes to your files sooner. Falling under the earlier mention of the importance of visibility, file integrity monitoring is crucial in keeping track of activity happening within your cloud environment.
6. Implement SSL certificates : SSL certificates enable encrypted communications between a web server and browser. SSL certificates are issued by Certificate Authorities (CAs), which are organizations that are trusted to verify both the identity and the legitimacy of the entities requesting the certificate.
7. Harden configuration management : Configuration management (CM) is an important piece of the DevOps concept of treating infrastructure as code. Since CM execute arbitrary code on infrastructure, you need to harden the systems to protect sensitive data. You can leverage tools such as chef-vault to encrypt sensitive data using public keys or implement file integrity monitoring, as suggested above.
8. Ensure safe access to production : If you’re practicing continuous delivery, you likely give developers access to production for efficiency purposes. Securing and monitoring activity across production servers is critical. You should be monitoring for events that could be suspicious, such as package installations and updates, to ensure that your CM system is the only entity managing your hosts.
9. Set up security alerting : You shouldn’t have to go looking for something anomalous. Setting up security alerting ensures that the second anomalous behavior is detecting, you’re aware of it. The key to useful security alerting is customization. By assigning different severity levels to different types of alerts, you can clear the clutter and hone in on anomalous, and possibly malicious activity.
10. Educate employees : Implementing security protocols is only useful when your employees understand how and why to use them. Employees should know the security risks associated with the business they do. When you execute a new security practice such as multi-factor authentication, you should educate your employees on why it’s so important and how to use it.
Emil Moe This might be helpful for you.
