What is CAPTCHA?
CAPTCHA (Completely Automated Public Turing Test to Tell Computers and Humans Apart) is a type of security measure referred to as a challenge-response authentication method that is used to identify users. With CAPTCHA, you are protected against spam and password decryption by completing a simple test that confirms you are human and not a computer trying to gain access to your account.
CAPTCHAs present problems that are challenging for machines to solve but relatively simple for people. Detecting stretched characters or numerals, for instance, or clicking at a certain spot.
CAPTCHA Usage Report
- reCaptcha by Google
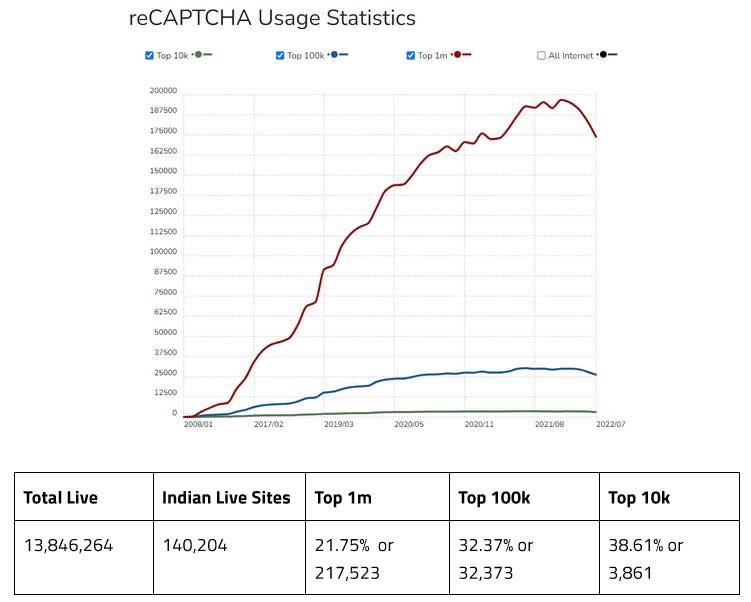
- hCaptcha by Intuition Machines
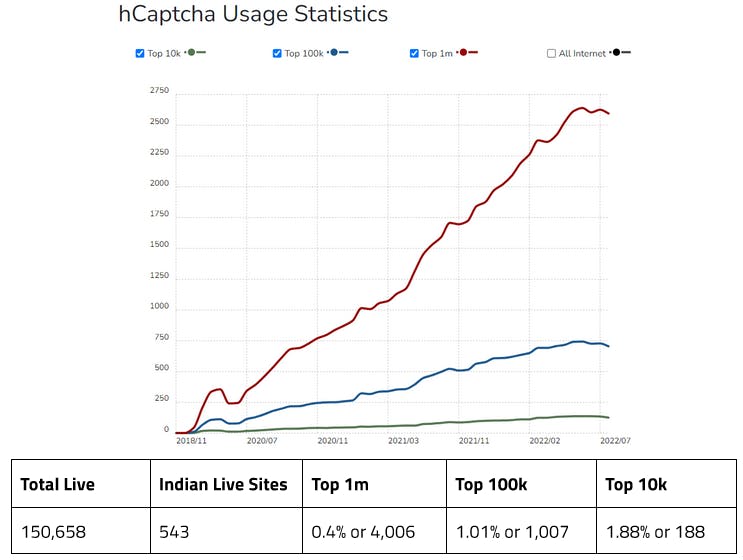
- Geetest by GeeTest
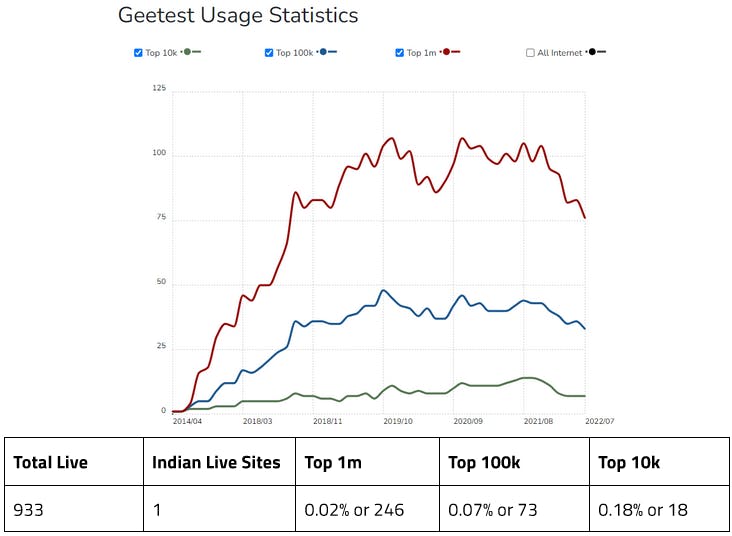
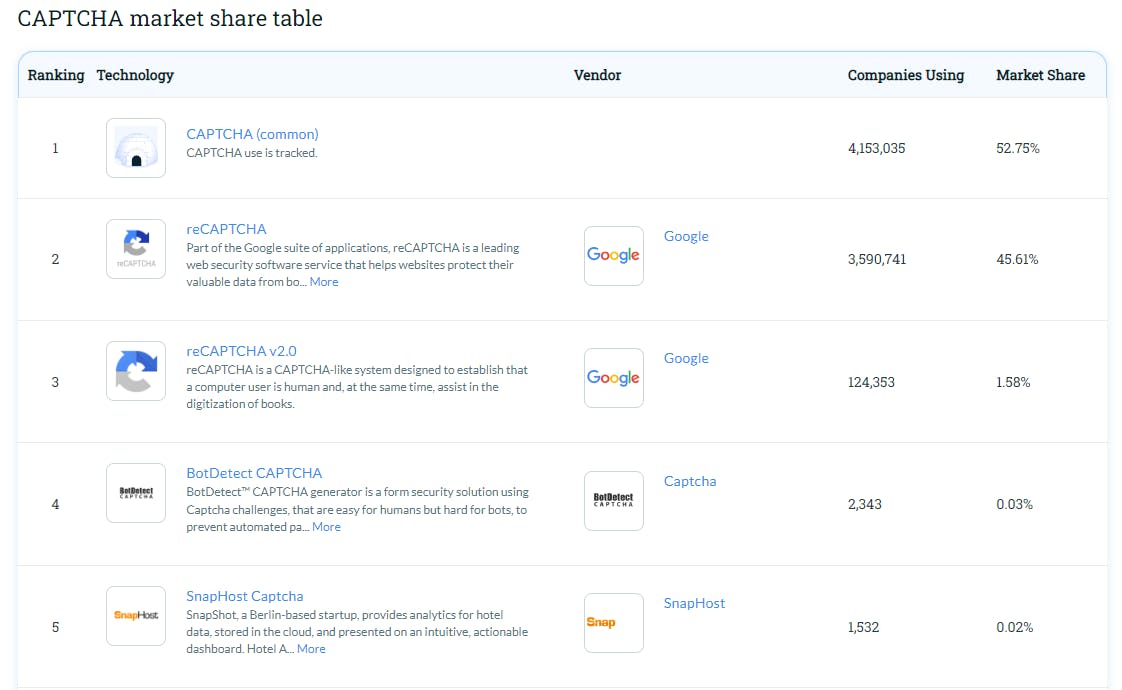
- CAPTCHA market share-
Types of CAPTCHA
- Normal CAPTCHA- Usually this CAPTCHA contains distorted but human-readable text in the given input field.
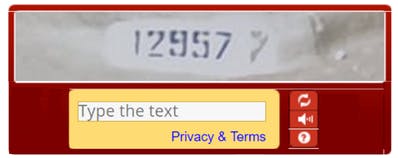
- Text/Maths CAPTCHA- Usually we have to answer the question or need to solve the mathematical expression.

Attackers Approach- To break normal CAPTCHA attackers will be using a driver object to find the element path. Once the page is loaded, the attacker will capture the element and update the value to the input field.
Image CAPTCHA - To get verified as a normal user we need to check all the right ones from the image.
reCAPTCHA V2 (Checkbox) - Automatically render the reCAPTCHA widget – To render reCAPTCHA only the JS resources and a g-recaptcha tag. Explicitly render the reCAPTCHA widget- We can render reCAPTCHA widget by specifying your onload callback function and adding parameters to the JavaScript resource.
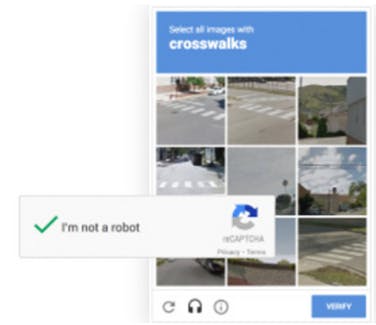
Attackers Approach- Buster is an extension available in a couple of browser marketplaces like google chrome Mozilla Firefox etc to solve difficult CAPTCHA's by completing reCAPTCHA challenges using the audio feature as a loophole available in widget. So, once we enable the buster, we will be seeing one extra icon of buster on the widget and upon clicking that it solves the given captcha.
Service Provider- Google, hCaptcha
Rotate CAPTCHA - We need to bring the shown object to the correct angle/ position.
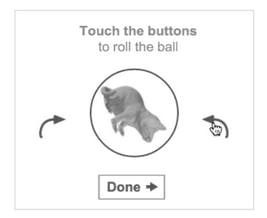 Service Provider- Funcaptcha by Arkoselab
Service Provider- Funcaptcha by Arkoselab
- Slide/Cappy Puzzle CAPTCHA - We need to drag the slider to place the missing object to right position.
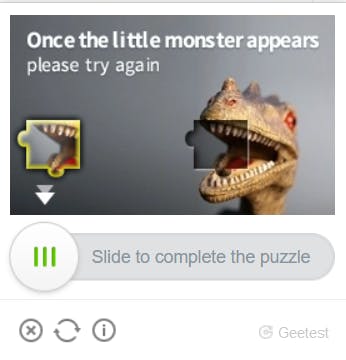
Service Provider- Geetest, Datadome
- reCAPTCHA V2 (Invisible)- Auto-binding- Add the JS snippet and the attributes like g-recaptcha and sitekey to the button. Add a callback function to handle completion of the CAPTCHA. Programmatically Invoke- To render programmatically need to add data-size='invisible'.
- reCAPTCHA V3- Whenever a user makes an interaction to the site the reCAPTHCA returns a score and enables the site owner to take required action.
Service Provider**- Google, hCaptcha, Geetest
Attackers Approach- The latest upgrade pushed by google is invisible reCAPTCHA where it doesn't serve the I’m not a robot checkbox instead from the previous behaviour of the user and from the browser cookies it justifies the action. So, if a user clears the cookies, then Google will enforce it to solve the challenge. So, if a user wants to bypass this then the user needs to add a code snippet to refresh the cookies on every request which is a bit of costly operation.
The other way to bypass this, an attacker can find the CAPTCHA section using the “inspect element” browser tool where the attacker will see that reCAPTCHA's iframe link contains the parameter “size=invisible”. So now the attacker can make a post call with parameters where the hidden captcha is located, to receive the solution at 2captcha level. Now the attacker needs to change the value of the g-recaptcha-response element to the token we have received. On the execution part, there is a form that should be submitted followed by the ID or name or any other attribute and then submit the form or there is a call back function executed when reCAPTCHA is solved. Attackers need to replace the g-recaptcha-response element with the token we receive from the 2captcha server.
CAPTCHA Solvers -
The more CAPTCHA market is growing it is also being noticed there are multiple CAPTCHA solving providers emerging and they are moving neck to neck in order to provide solutions for all types of CAPTCHA. Some of the list are below:-
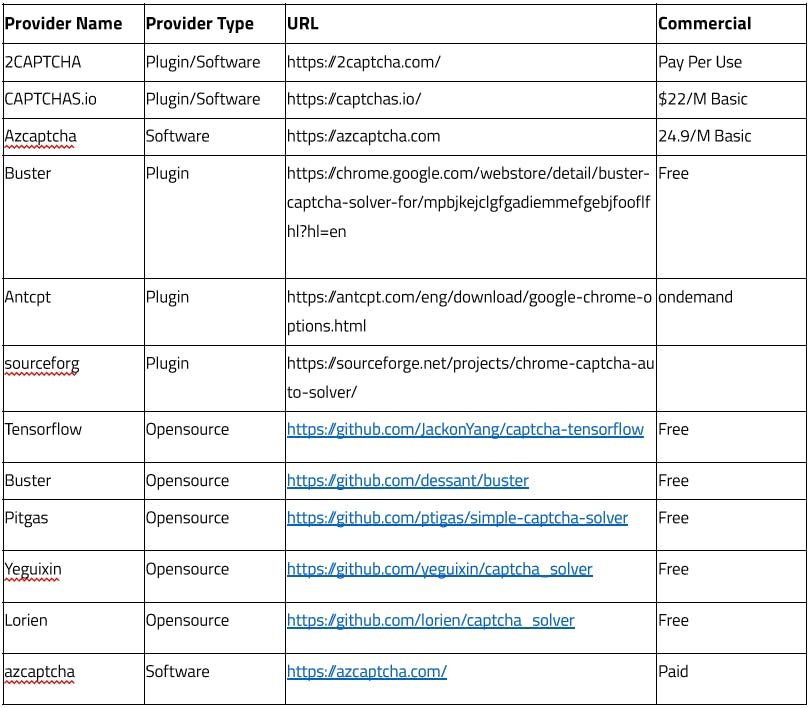
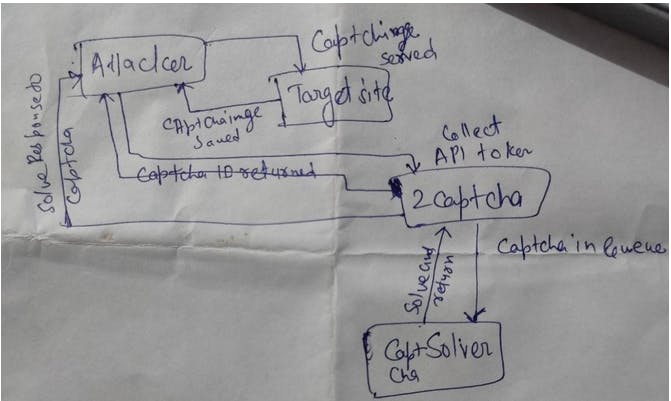
What goes behind the CAPTCHA automation process?
While running the automation, attackers target the iframe source section and the URL of CAPTCHA image to save this locally. Using the API key provided by 2CAPTCHA/ CAPTHCAS.io it triggers a post request to collect the CAPTCHA ID. Workers get assigned to solve the CAPTCHA and then submit the solution. If the CAPTCHA is not getting solved, we get a response “CAPTHCA_NOT_Ready” and the script keeps trying every 5th seconds. We can iterate this process to solve each CAPTCHA.
What level of user experience are getting killed just by CAPTCHA alone-
Smart automation can easily bypass the CAPTCHA.
- Due to the CAPTCHA limitation and design flaw it is easier to build or utilize available solutions to crack all CAPTCHA flavors.
- No trace back to the action taken that means no justification for FN and FP’s
- For a normal user the avg CAPTCHA solve time is 5-20 sec which irritates the user and if there is a system which understands the user behavior based on interaction trend, fingerprinting, IP reputation, cookies and more, then this window time can be eliminated.
